
Introduction
More individuals and organizations presently utilise the cloud in some way, some of the time without acknowledging they are doing as such. Unfortunately, being uninformed of utilising the service also implies that individuals are not as protected as they ought to be and it is turning out to be increasingly significant to know how secure your data is on the cloud. Cloud computing is a broadly preferred platform across associations. The fluid data exchange and the freedom to access data 24 hours permits organisations to operate constantly. Even though the cloud service is very convenient to use, one ought to understand that data may be comprised if organisations do not take suitable measures. The huge collection of raw and processed within the cloud draws the attention of hackers to lurk around, resulting in possible data breaches. End to end encrypted data rooms are a better way of using cloud computing securely.
Significance of cloud security
According to a recent study, 1 of every 4 organisations utilising public cloud services has faced information theft by a hacker. Additionally, 1 out of 5 has encountered an advanced attack against their cloud system. In the same research, 82 per cent of organisations revealed that they store sensitive data on the cloud. With 95 per cent of companies around the globe utilising cold services nowadays, it is crucial that everybody assesses their cloud security and develop a method or technique to protect their information.
Methods that can help you protect your cloud data from hackers
Some of the methods that can help you protect your cloud data from hackers are:
-
Utilise encryption – Before uploading data into the cloud, try to encrypt it since this is a great security measure against threats from hackers. Utilise local encryption as an extra layer of security. Encryption helps to ensure that the service provider, service administrator and any third party does not have access to your data. Before choosing a service provider, always try to pick a service provider who provides essential data encryption.
-
Read the user agreements – Before sign-up for a cloud service, make sure you read the user agreement entirely. It consists of important information that explains how the cloud service protects your data from hackers and regardless of whether you give them consent to sell or use your data in any way possible after you have signed up. Never sign-up for a service online without completely understanding what each clause means in the user agreement. Every time the service provider updates their privacy policies, it will inform you through a text message, email or a notification message once you log in. Always make sure you read the text messages or emails sent to you by your service provider to assure that the changed privacy policy does not negatively impact your data.

-
Do not share your personal information – Sometimes your personal information might appear to be harmless, however, in case it falls into a hacker’s hands, it can leave your identity unprotected. Never reveal your birthdate or your mother’s middle name in public openly because they are frequently asked questions to confirm your identity. You also need to avoid sharing your personal information, like your first pet’s name or the street name you lived in while you were growing up with people you do know trust or know personally. Although you might know or trust someone blindly, try to avoid sharing your social security number’s last four digits even with them. A few of the service providers will permit you to select the questions you will need to answer for verification. In case, you get the choice, select questions whose answers you can easily recall, however, the majority of the individuals will not easily find out about you, for example, where did you go on your first date or an embarrassing name your sibling calls you.

-
Utilise a strong anti-spyware program – Since the cloud helps to transfer data over the Internet, it is crucial to have a strong anti-spyware program installed on your personal computer, tablet, mobile phone or some other gadget. These types of programs help you block any suspicious mail, website link or download. Some anti-malware programs offer features like wiping out data remotely when your laptop or smartphone gets stolen, backup and even location services.

-
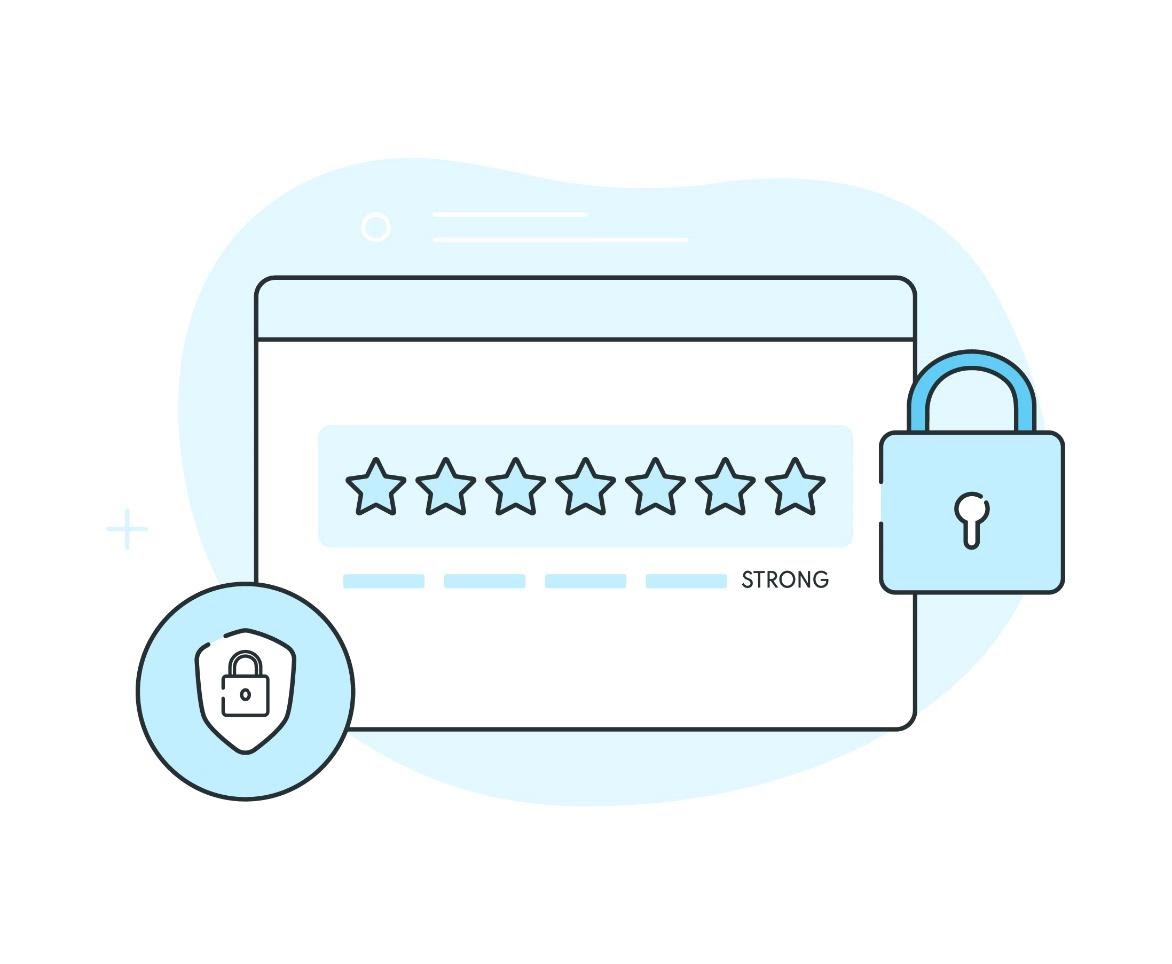
Create a strong password – A strong password is necessary for each account you have, however, particularly with regards to protecting accounts that you use to store your personal information. More than 80 per cent of attacks are because of weak passwords which implies that you need to be persistent while creating yours. Try to create a password that has 15 or more characters and never less than 8 characters for the best protection. Abstain from using information that people can easily guess, for example, your full name, birthday, the company’s name you are currently in or the name of your pets. Create a password using symbols, numbers, uppercase and lowercase letters. Lastly, try to change your password as frequently as possible and avoid using the same password for all your accounts.
-
Utilise two-factor authentication – Whenever you get the option, always utilise two-factor authentication. This implies any person who tries to sign in to your account will require you to provide more information rather than just the password. Some of the most common methods of authentication are answering a personal question or inputting a PIN that your cloud provider has messaged or emailed you. You could also try to download an authenticator application. Not every account would automatically request you to set up two-factor authentication, so make sure to take a look at your setting to check whether the option is available or not.

-
Update your operating system – Sometimes, you might be tempted to ignore the notifications that alert you to update your operating system, however, these types of updates are usually crucial for ensuring your computer and information is protected. They typically find and fix bugs or threats in your system that leaves your computer at risk. By overlooking them because of their occasionally inconvenient timing, you tend to set yourself up for even a bigger inconvenience in the future. Ensure you update your operating system once every 6 months.

-
Set up your privacy settings – After you have signed up for a specific cloud service provider, reconfigure your security settings to assure that you are not sharing your data through the applications you have connected your service provider to. You need to also decide how long your chosen service stores your personal information and which kinds of information it could fit your application or gadgets. After initially setting your privacy settings, check and configure your setting again every 3 to 4 weeks to make sure you stay safe.
-
Use public WiFi cautiously – When you could create creative passwords, utilise firewalls and provide anti-spyware programs when you utilise your house’s Internet connection. You cannot be 100 per cent sure that the public Internet connection is secure. When you try to use a public connection, check the source of the connection before connecting to it. Try to avoid using or connecting to a WiFi connection if you cannot confirm the source since hackers tend to utilise open WiFi connections to steal your data. They do not even need an expert when it comes to using hacking. All they need is a small gadget and to sit within 100 feet of you while you are using the connect. To protect your data further, keep your WiFi option turned off unless you are ready to log into a verified or trusted Internet connection. Always utilise a VPN whenever you are viewing personal or private in public.
-
Manage your user access – In case you run a business, most workers in a work environment does not need to access each application, each piece of data or each file or folder on the cloud service. Setting appropriate levels of authorisation with an IAM (Identity and Access Management) plan helps to assure that every worker could just see or manipulate the apps or information essential for the individual to complete the tasks they were assigned to them. By assigning an access control not just helps to keep a worker from accidentally altering data that they are not authorised to access, however, also helps to prevent hackers from viewing or manipulating the data after stealing a worker’s login details. It ought to also be noticed that several regulatory compliance laws, for example, HIPAA (Health Insurance Portability and Accountability Act), FINRA (Financial Industry Regulatory Authority) and numerous others, need these kinds of security measures. In case workers have access to everything can get gets deceived by a phishing email and unintentionally gives their sign-in credentials to your cloud. If you do not have the in-house time or ability to deal with this user visibility and control yourself, make sure you work with a certified IT specialist to assist you with getting this set up appropriately. You could also examine the ongoing management of every cloud IT services by signing up with a managed services provider who could guide you regarding which employees you need to give access to, according to their roles.
There are existing free solutions which help to improve the protection of your sensitive data. Dastafilez has shown to be a solid and cost effective way of storing data.
