Introduction
The quick development and associated innovations of information communication and technology have integrated a lot much simplicity to individuals’ work and lives; cutting distances among people and obscuring the lines between countries. Computer information network technology has advanced rapidly in the modern world, resulting in the most ubiquitous information network. People actively engage with each other over the internet while computer network security concerns pose a significant danger for information communication.

The challenge of computer network security is a difficult one to tackle, but data encryption technology has made a substantial contribution to resolving it. With the advancement of the information age, computer data encryption technology has also undergone a deeper examination; researchers should continue to pursue technological innovation, and data encryption technology has developed into an effective guarantee for maintaining computer network security. The data encryption system makes extensive use of data encryption and digital signature technologies, which not only address the key management issue but also secure the data’s integrity and nonrepudiation. The worldwide encryption programming market size was assessed to develop from USD 9.8 billion in 2020 to USD 20.1 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 15.5%.
What Is Data Encryption?

Data Encryption is a cybersecurity technique that keeps the data secure while it travels from one point to another over an insecure internet channel. While providing security against traditional and non-traditional cyber-attacks, encryption lays its foundations on storing secured data on cloud platforms or computer systems. The canvas of data encryption covers both types of data i.e., data at rest and in-flight data. Encryption algorithms convert plain text into the scrambled form i.e., ciphertext which can only be decrypted by the authorized parties having the relevant keys. It comes under the realm of cryptography, which is generally characterized by confidentiality, authenticity, integrity, and non-repudiation.
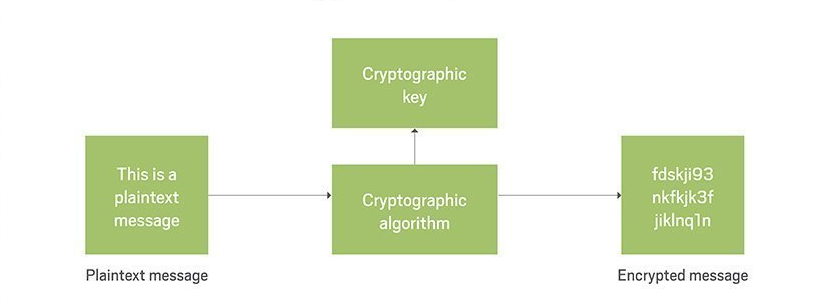
Considering the end-user requirements, the realm of data encryption is generally classified into two types: asymmetric encryption and symmetric encryption:
Asymmetric Encryption – Generally known as public-key cryptography, asymmetric encryption processes encrypt, transfer and decrypt data using two different sets of cryptographic keys. These two keys are called “private key” and “public key”. As suggested by the title, the public key can be shared with any set of audiences but the private key should remain confidential and protected. The public key is used for encryption; the secret key is used for decryption. This type of encryption model can ensure the sanctity of information traveling over an insecure channel by the use of digital signatures. When one user directs data encrypted via the other user’s public key and the receiver receives the encoded information using their secret key, the procedure is referred to as asymmetric encryption. It has the advantage of having open encryption keys, which eliminates the need for users to shuffle between public and private keys; it also makes it simple to obtain a digital signature, which guarantees the integrity, verification, and confidentiality of the transaction process, and can potentially avoid DDoS attacks. Asymmetric encryption has the setback of being computationally complicated, as well as having a sluggish decoding speed.
Symmetric Encryption – These encryption algorithms encrypt and decrypt the electronic message using the same cryptographic key. In essence, it might be very fast as compared to asymmetric encryption modules, but with one inherent bottleneck, the sender must share the encryption key with the recipient before the decryption could take place. Symmetric key encryption technique encrypts and decrypts using a single key, and both parties must have access to and maintain the privacy of the communication. When delivering data to both parties, each party encrypts it via pre-owned encryption keys, and the receiver can view the required content with the relevant decryption key. Generally referred to as the clandestine key encoding, symmetric encryption provides the benefits of agility and safety. It also has certain drawbacks: the key cannot be discreetly assigned; there is no way to detect a key leak automatically. More so with the increase in the number of individual users over a network, the number of keys might exponentially grow resulting in the potential issue of message acknowledgment.
Technical Framework of Data Encryption
Generally, the plaintext is referred to as plaintext, whereas encrypted-text is referred to as ciphertext. Encryption is the procedure of transforming plain-text to cipher-text. Decryption is the opposite process, that is, the course of transforming ciphertext to plaintext. To encrypt/decode part of the special data and; administer the conversion from the plaintext to ciphertext, the key may constitute statements, numbers, or words. The terminology “key” denotes both the encryption key and the decryption key. The cipher system signifies the titles of the encryption and decryption algorithms. In certain instances, the encoding and decoding keys are distinct, leading to a non-symmetric kind of encryption. The progression of data encryption or decryption is exhibited as follows:
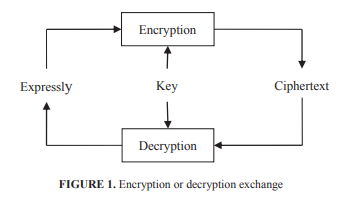
Given the characteristics and technical frameworks of asymmetric and symmetric key encryption, the on-ground applications entail two types of encoding technologies, complemented via a combination of DES and RSA for network data transmission. Individually, the DES (Data Encryption Standards) is used for encoding of network transmission while RSA (Rivest–Shamir–Adleman) ensures the data security while provisioning improved speeds of encryption and decryption.
The following figure illustrates the combination of DES and RSA.
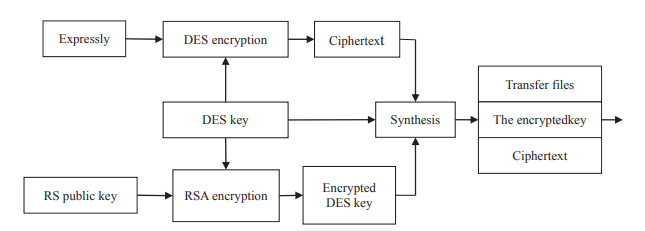
As a first step, the relevant DES algorithm is employed to encode the plaintext into ciphertext via symmetric key cryptography. Secondly, the associated RSA’s public key is utilized to extract the DEA (Data Encryption Algorithm) which can then encrypt the ciphertext in conjunction with the network of the stakeholder on the receiving side. Finally, once the ciphertext information is acknowledged, the receiver can decode the key with his confidential key to acquire the DES, which can certainly decrypt the ciphertext back to plain text.
Although DES can be used in a wide array of cybersecurity applications and is available on many public platforms, the key length of 56 bits makes it vulnerable to attacks and its encryption strength falls short of advanced security requirements. To cater to this requirement, the mixing of two 56-bit keys while encryption and decryption result in a key length of 112 which significantly increases the encryption power. This phenomenon is referred to as 3-DES.
The schematic design of the 3DES method is given as follows, where the keys K1, K2 are created randomly.
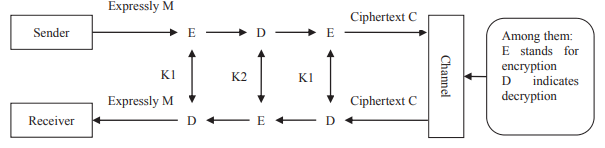
Triple DES algorithm implementation includes two classes: DES class and THREE class.
The main functions of the DES class:
public static byte[ ] encrypt(byte[ ]oword64, int[ ][ ]iSubKeys) // encryption
public static byte[ ] decrypt(byte[ ]bCipher-text, int[ ][ ]SubKeys) // decryption
The main categories of functions are:
public static byte[ ] encrypt(byte[ ]oword, int[ ][ ]SubKeysl, int[ ][ ]SubKeyS2) // decryption
public static byte[ ] decrypt(byte[ ]sword, int[ ][ ]SubKeysl, int[ ][ ]SubKeyS2) // encryption, return plaintext
The security of RSA is based on a huge number of decompositions. Both the cryptographic keys i.e., public and private keys are formed by prime numbers which are essentially more than 100 decimal digits. The application of the RSA algorithm entails the production of keys, encryption of data, and decryption of data. The procedure of implementing the RSA algorithm is outlined as follows:
- Definition of variables using a vast number of Java
BigInteger(). - Creation of the key via Boolean generator
PQNTED(String e). - Encryption process via using
public String encrypt(String msg, BigInteger pbkey, BigInteger n)while finishing the process viacopyBytes()transfer function. - Decryption process via
public String decrypt(String msg, BigInteger prikey, BigInteger n)
RSA must lay its foundations on the greater number of operations, based upon the premise that the deployment and implementation of the algorithm may entail a lot many functions of additions, subtractions, multiplication, addition, modular expansion as well as modular inverse operations. It may lead to a significant drop in RSA’s performance benchmarks and efficiency in comparison to various other algorithms (special reference to DES – the go-to symmetric encryption module). The aforementioned disparity in process agility can be attributed to system configurations performed for exchanging the produced keys, via utilizing RSA.

Keeping in view the scale and scope of cryptographic applications, digital signature technology can be significantly employed in the RSA’s digital signature system. To achieve the full functionality benchmarks of digital signature technology, one condition needs to be fulfilled: none other stakeholders could fake a signature, and that all the signatures can be validated with full-channel traceability. Digital signatures powered by RSA utilize the public key cryptographic approach – as depicted in Fig. 4. Being very similar to cyphers, on one hand, RSA digital signature schemes differ in the approach of signing and verification on the other guaranteeing that no signatures can be forged. Java classes can be used to generate both public and private keys in the realm of RSA. The initverfy() method of the signature object accepts the public key, performs the verify() function, and compares the original data to the signature information.
Dastafilez - An Innovative Approach to Data Encryption
Dastafilez can be employed for the use instead of Dropbox and WhatsApp; Dastafilez, an innovative virtual data room, offers one of its kind solutions to offer privacy and protection of classified information via multi-factor authentication, end-to-end encryption, and advanced authorization modules. It essentially is a platform with controlled access management to share any important information or documents in a secure manner. Being a cloud-based data room platform, Dastafilez offers a host of innovative features which certainly form the unique selling propositions for the subject application. Unlike other communication applications, Dastafilez operates on true end-to-end encryption i.e., encryption is not an opt-in feature, rather is implemented across the board for all the relevant information records and subsequent sharing. Coupled with the features of Zero-Knowledge Architecture and Immutable audit trails, Dastafilez stands out to be a strong contender in the domain of secure communication platforms.
Conclusion
With the evolving nature of cyber threats, more and more efforts are being directed to develop counter measures which are efficient, effective, and optimized for any kind of traffic over an insecure internet channel. One of the widely used techniques in this regard is data encryption; converting data into ciphertext which can only be decrypted by the other party if provisioned with the relevant key. It ensures confidentiality, integrity, and non-repudiation for confidential files and communication. While there are multiple off the shelf techniques available for data encryption, essentially, they all belong to the domain of cryptography (implementation of red-black engineering via thorough segregation between circuits and equipment used to carry plain text classified information (non-encrypted - RED Signal) and secured circuits and equipment that carry encrypted information (BLACK Signal). Given the context of COVID-19, where almost every domain of business is either being supported or replaced by online platforms, encrypted communication becomes a key factor for ensuring that the right information reaches the right stakeholder at the right time. Not only will streamline the business operations, but also will steer the enterprises towards achieving competitive advantage. Those organizations who promptly focused on information technology in general and data encryption frameworks in particular in the pre-COVID times survived the economic downturn caused by the global pandemic while those who were in the reactionary mode suffered blatantly. Undoubtedly, deployment of encryption frameworks would require sheer focus coupled with a good amount of capital investments, but keeping in view the benefits of it, one can easily expect a very high return on investment (ROI) in a shorter span of time.
