Introduction
With rapid digitization, more and more data is being recorded and stored by enterprises. Not only does this data help the management to extract critical business insights but also steer the organization into the strategic dimensions for achieving over-arching objectives of business growth and brand reputation. While data analysis adds a significant value to informed decision making, it may also pose cyber-risks which if materialized can cost organizations their fortune, both in terms of revenues and brand reputation.
Kaspersky defines data compromise or breach as:
“A data compromise or breach exposes confidential, sensitive, or protected information to an unauthorized person. The files in a data breach are viewed and/or shared without permission.”
As the proliferation of network and IoT devices increase in the business environments, certainly more avenues become available for back doors and thus data can get compromised. Such data compromise or breach can cast far-reaching financial impacts for the organizations. With the smart use of blockchain technology many of these risks can be mitigated.
Data-Compromise Cases
With evolution of technology, the nature of cyberattacks is becoming more advanced which are surely more difficult to detect and mitigate. In order to get a holistic view of the impacts of data compromise or breaches, the following use-cases can be considered.
1. Microsoft – January 2020
At the start of 2020, a user database of customer support was accidentally exposed online due to some configuration errors. Although the user’s information was stored in the form of anonymized analytics, yet the exposure took place. As per the subsequent research, more than 250 million customer records spanning over the duration of 14 years were compromised. These records included email addresses, IP addresses, and some other relevant details. Similarly, the company claims that a state-sponsored cyberattack was carried out by a Chinese firm, Hafnium; it impacted 30,000+ organizations of the US including some government and federal agencies.
Microsoft certainly reacted to the attack and data was restored yet shares of Microsoft took slumped and brand image was hurt. Certainly, a specific segment of customers lost their trust in Microsoft which isn’t good at all for any tech enterprise. More so, the company came under the spotlight of regulators, thus impacting the ease of doing business.
2. Facebook – April 2020 & October 2021
Being the market leader in social media networking, Facebook sets very high benchmarks of data security and integrity. Yet a very significant data breach took place in April 2020, when COVID-19 protocols started to take effect; over 267 million Facebook profiles were offered for sale on the dark web. This breach included personally identifiable information (PII) including phone numbers and email addresses. This leaked information could potentially form the basis of spear-phishing campaigns aimed at collecting the user credentials via bogus emails or SMS alerts. These records came with a princely price tag of $600, while the organization faced a lawsuit thereby and a hefty amount of fine damages.
Very recently, all the products of Facebook Inc. i.e., Facebook, Facebook Messenger, WhatsApp, and Instagram went offline. While official sources say that outage was due to a configuration error, some cybersecurity officials quote that data of 1.5 billion users is up for sale; it also includes emails and phone numbers. This 6-hour outage has caused a loss of 6 billion U$D to the net worth of Mark Zuckerberg, the founder, and CEO of Facebook Inc.
3. Zoom – April 2020
As the restrictions of COVID-19 took effect in April 2020, most of the business went online with Zoom being the most preferred source of audio and video communication. The tech firm wasn’t prepared to handle the huge influx of users and resultantly, over 500,000+ Zoom teleconferencing accounts became available for sale on dark-web for as little as $0.02 per account. Malicious hackers quickly employed the compromised passwords to launch the credential stuffing attacks which allowed them to access even more accounts. Resultantly, hackers could log into live meeting rooms, create chaos, and record classified information.
4. Twitter – July 2020
Twitter, the social media powerhouse, suffered an unprecedented attack in July last year when 130+ celebrity accounts were hacked by cyber-criminals. These accounts included the ones of Barack Obama, Kanye West, Elon Musk, Joe Biden, and Bill Gates. Reportedly, the criminals collected 100,000+ USD via this attack. More so, they also contacted the Twitter employees as their fellow workers and asked for passwords of the organization’s internal support system; this allowed the hackers to get access to further employee accounts, and classified user information was compromised.
5. LinkedIn – June 2021
A few months ago, LinkedIn data of over 700 million users was posted on the dark web for sale. It was hacked by the criminals using data scraping techniques i.e., via exploiting the network’s API before publishing the dataset. This data breach was directly in contradiction to LinkedIn’s terms of service as the leaked data included email addresses, phone numbers, gender, and location records information essentially forming the basis of social engineering attacks.
6. Android by Google – May 2021
Being the most-used mobile operating system in the world, Android has been equipped with advanced security frameworks. Yet, due to some configuration errors of cloud services, the personal information of over 100 million users of the platform got exposed. The source of this compromise was rooted in 23 apps, coupled with unsecured databases.
7. Volkswagen & Audi – June 2021
Famous automobile manufacturers i.e., Volkswagen & Audi, got affected by the incidence of a data breach that happened in June 2021; personal information of 3.3 million customers in the United States and Canada got compromised which included names, email accounts, vehicle type, leasing information, make, colors, and types, etc. In addition, hackers got access to driving license numbers, dates of birth, social security numbers, and tax ids were also exposed.
8. Astoria Company – January 2021
Astoria Company LLC is a lead generation and exchange organization, based in the United States. In January 2021, 30 million records associated with Astoria Co. were found listed on the dark web for sale. But it was only the tip of the iceberg as leaked data cumulatively contained the profile information of 400 million Facebook users and 300 million records of Astoria Company customers alongside email addresses, postal addresses, and IP addresses. Astonishingly, it also contained bank account information, email transaction logs, and medical history too.
9. ClearVoiceResearch - 2015
Being a research organization, ClearVoiceResearch has records of responders and survey participants stored in its databases. Very recently, such data spanning the timeframe of August & September 2015 was put to sale on the dark web. Essentially, it impacted 15.7 million users and has critical records like contact information, passwords, political affiliations, and ethnicity, etc. This data could easily be used for customer profiling and segmentation in a commercial or political context.
10. Yahoo – 2013
Being considered the most significant data breach in the IT industry, 3 billion accounts of Yahoo were affected by compromised data in 2013. Now taken over by Verizon, the data breach resulted in a much lower valuation of the company’s assets (350 million lower) than the original offer. The compromised data included the credentials, preferences, contact information, and email addresses, etc.
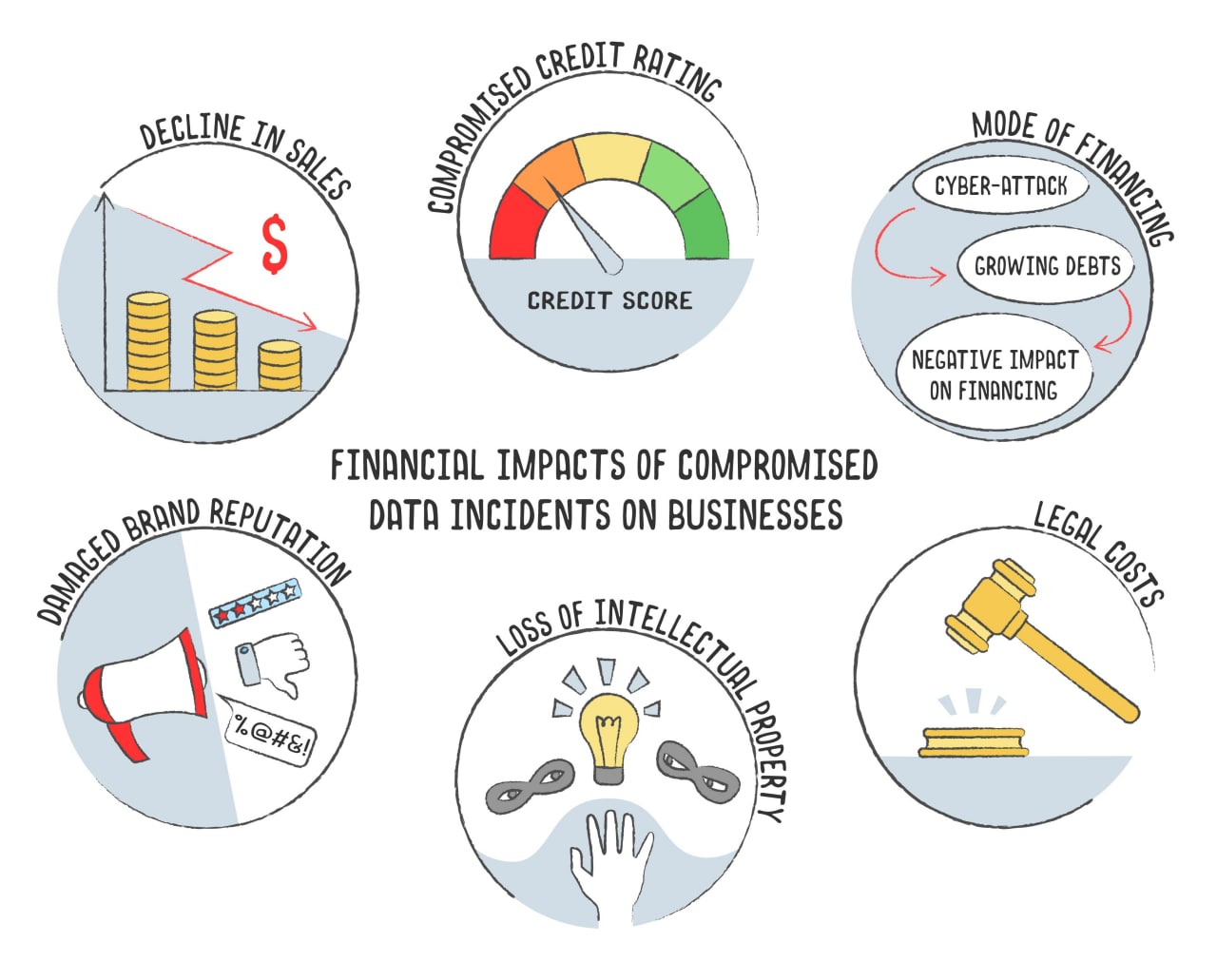
Financial Impacts of Compromised Data Incidents on Businesses
Data breaches via cyber-attacks caste multi-faceted impacts on businesses, a few of which are outlined below:
1. Decline in Sales
The foremost impact of any data breach is the decline in revenues; it flows from the fact that enterprises lose their credibility amongst customers, and subsequently, they look for comparable alternatives where the personal information remains private and safe. The decline in sales drives the decline in overall revenues and the situation gets further exacerbated when long operational downtimes become crucial for data recovery. According to the National Bureau of Economic Research (NBER - US), “after suffering a breach of customers’ personal data, the average attacked firm loses 1.1 percent of its market value and experiences a 3.2 percentage point drop in its year-on-year sales growth rate.”
2. Compromised Credit Ratings
Investment is a critical component for the survival and growth of any business; the damages caused by data compromise incidents don’t stop at declined revenues but go a step further and diminish any chances of future investment as the affected organization becomes a risky profile. Ultimately, it affects the credit ratings of the enterprise, resulting in low investor confidence.
3. Mode of Financing
The preferred mode of finance for the cyber-attacked organization shifts from stock issuance to loan bonds; when capital is borrowed, it is done so at longer maturity durations, so as to minimize the exposure and the rollover risk. At the same time, the increasing debt component is reflected in the financial statements and financial ratios adjust themselves accordingly, thus casting negative impacts onto the overall business.
4. Damaged Brand Reputation
Compromised data incidents also damage the brand reputation of the enterprise; consumers want to make sure that their data is in safe hands while data breaches not only affect customer retention but also the opportunities for new customers acquisition become bleak. This automatically translates into lower revenue levels and thus stagnant or negative growth.
5. Loss of Intellectual Property
The intellectual property items like designs, blueprint, and growth strategies can also be compromised with data breaches; an enterprise can lose its competitive advantage in any given domain when the aforementioned items go into the wrong hands. This materializes into a major setback as far as business growth and sustainability are concerned.
6. Legal Costs
Generally, the cases of data breach go into legal litigation; it not only causes organizations huge costs but also a lot much time is wasted in following the legal proceedings. More so, the focus of the organization may shift from revenue generation to legal hearings which may impact the business in the long-term.
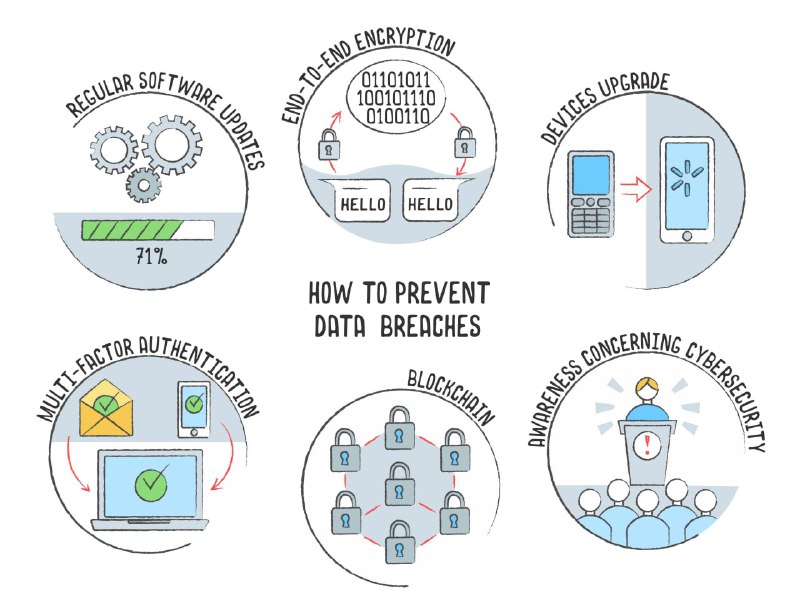
How to Prevent Data Breaches
In order to prevent data compromise incidents, a proactive approach can be used to counter any prevalent risks.
-
For multiple platforms, enterprises should regularly update and patch the software so as to cover any possible vulnerabilities.
-
Use end-to-end encryption (software and tools that are set up that way) on any sensitive internal or external communication such as offered by Dastafilez.
-
Devices should be upgraded when the relevant software component is no longer supported by the manufacturer.
-
Multi-factor authentication and strong credentials policy can be enforced to promote better cyber-security practices at individual and collective levels.
-
Data stored on any 3rd party server may be a source of risk. Using a scalable and low-cost blockchain for data storage significantly reduces the risk of losing data.
-
The most important part is creating awareness amongst the masses in general and employees in particular related to cybersecurity and the ways in which personal data can be compromised.
Conclusion
The advancements in technology come with a cost, which is generally manifested in the form of data breach incidents. By such compromises, the consumer data which can be leveraged to formulate effective business strategies become a source of liability and results in a loss in revenues alongside bad word of mouth. In order to mitigate any such threats, a multi-pronged approach is required to pre-empt the data compromise cases; not only do all relevant stakeholders need to be on the same page but also the tech infrastructure should be updated to avoid any malicious user accessing the classified database. Surely, getting there would require some serious capital investment which can guarantee higher ROIs but, if not done promptly can have significant opportunity costs for the enterprises.
