
Introduction
With the ever-growing global internet and smartphone penetration, digital technologies are evolving and have certainly taken the centre stage in all facets of business and personal domains. Due to the prevailing COVID-19 lockdowns in place, the dependence upon messaging platforms has significantly increased for the purpose of information communication. As 79% of the world population owns smartphones, the use of internet-based instant messaging applications has become an integral part of life that provides the convenience of information sharing with almost no costs involved. On the flip side, the online presence is always coupled with the existence of information capturing backdoors for the unintended malicious uses; backdoors embedded into the instant messaging (IM) apps can track every online activity of the user, which certainly compromise the privacy and integrity of the information but can also put the safety of the novice users in jeopardy. Even the platforms of the tech giants are susceptible to threats and attacks, and continuous efforts are being made to ensure a safer user experience. These efforts pivot around minimizing the information leakage risks and the subsequent attacks so that any negative consequences can be mitigated. While a host of messaging platforms are available, which guarantee security, privacy, and integrity of the data communicated over the internet link, Dastafilez stands out owing to its unique features, which are a result of rigorous need-product mapping and continuous innovation frameworks.
Importance of Secure Communication Systems
With the global internet users crossing the 4.7 billion mark, more and more processes are becoming digitized; as the number grows, the information shared via instant messaging platforms also grows, presenting an opportunity for information capturing and retrieval via cyber-attacks. Communication systems have connected individuals as well as enterprises across the globe, thus carrying the crucial information to be communicated. Not only the individual conversations, but these systems also play a pivotal role in application to peer (A2P) processes; digital financial services significantly rely on A2P communication. Given the importance of securing the information over the internet, secure communication systems become critical as their mandate is to provide such a technical framework so that attacks can be minimized and risks can be mitigated, all while ensuring privacy, confidentiality, and integrity of the information.
Characteristics of Secure Communication Systems
Secure Communication Systems are characterized by end-to-end encryption to minimize the impacts of any security or privacy risks prevalent in accordance with the backdoors. The security framework that powers the messaging systems provide comprehensive protection in the lights of advanced viruses and spam. It usually lays its foundations on public and private keys-based cryptography and can provide message filtering without taking into account the content or the associated language.
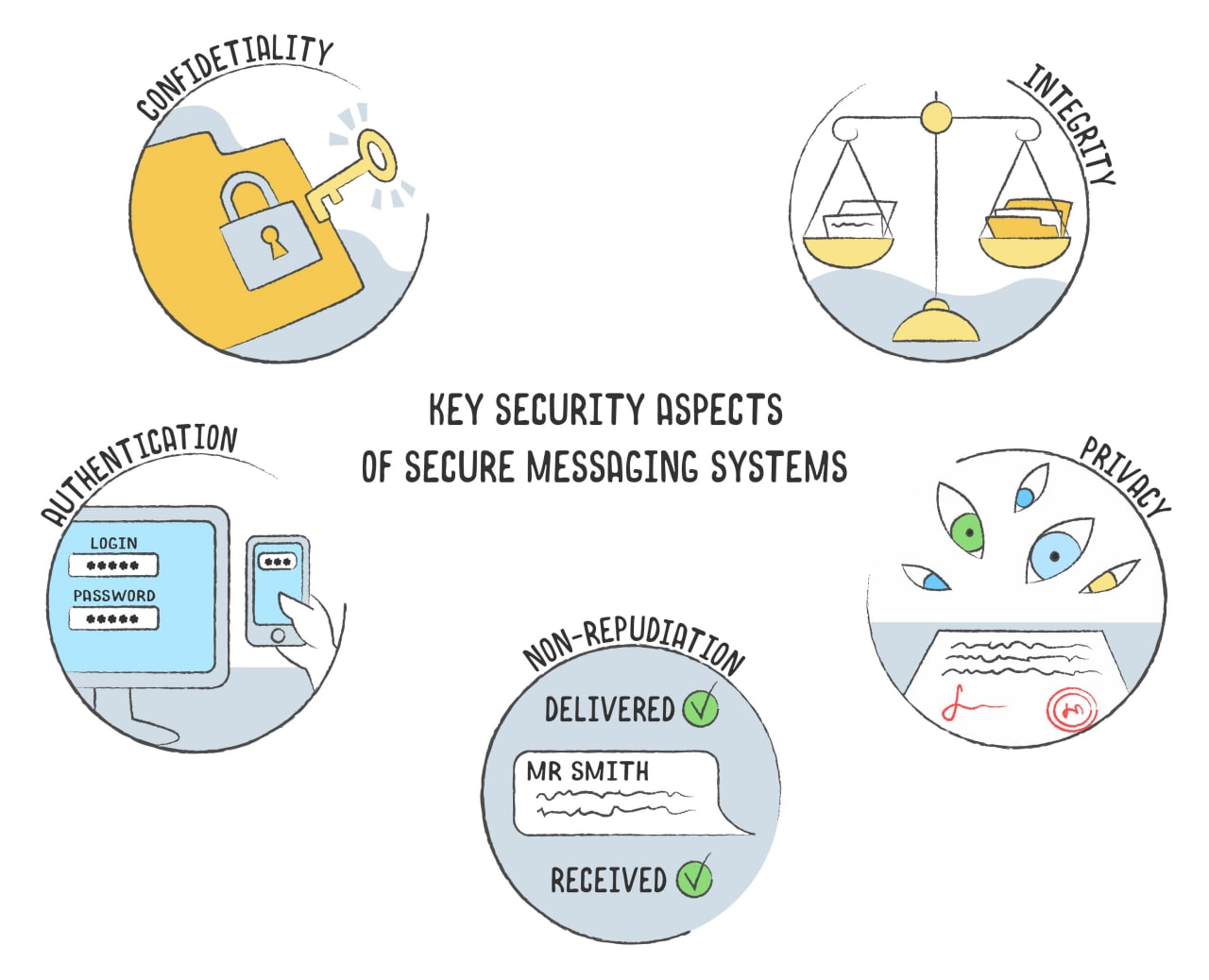
Key Security Aspects of Secure Messaging Systems
For being categorized as a “Secure” communication system or platform, the following aspects of the security must comprehensively be addressed from all dimensions.
1. Confidentiality
In any communication process, at least two parties are involved; confidentiality signifies that the information amongst the communicating parties over the internet channel can only be read by the authorized users, after performing the relevant due diligence. To ensure the confidentiality of the messaging content, cryptographic techniques are utilized which involves sharing the relevant keys to the concerned users on regular timeframes.
2. Integrity
As the information travels over the non-secure channel of the internet while communicating with other parties via messaging platforms, integrity needs to be ensured i.e., content isn’t edited or modified during the transfer between the concerned parties. It becomes particularly crucial when the malicious users have the capability to eavesdrop on the communication medium and can subsequently modify or even replace the content.
3. Authentication
To ensure the sanctity of the messaging service, it is of utmost importance to authenticate any entity before the start or even within the communication process. Authentication mitigates the risk of any malicious attacks by which attackers can impersonate themselves as genuine users and can access classified or confidential information. Authentication can be of two types; weak and strong. Weak authentication would entail a single factor authentication only i.e., pin or password-based authentication. Strong authentication comprises multiple-factor authentication frameworks i.e., one-time passwords and certificate-based authentication (CBA).
4. Privacy
In the realm of digitization, Privacy signifies the control of the user upon the scale and scope of information that can be shared with or accessible by the outside entities i.e., regulatory bodies, service providers, and security institutions. For a communication service to be secure, it needs to ascertain that the privacy of the users is ensured and no metadata e.g., location, name, contact, operation system, phone storage media is shared with the third-party entities without due permissions.
5. Non-repudiation
Given the context of the security risks whereby malicious attackers can impersonate as the genuine user and can send messages to multiple parties, non-repudiation property of the IT frameworks becomes important i.e., any communication made over the internet channel can’t be denied by the relevant parties. The non-repudiation feature is incorporated in the communication platforms by tracking, tracing, and proving the source of the message, thus minimizing any chances of forgery.
Description of Attacks & Breaches – Messaging Systems
While one delves into the details of key characteristics of a secure messaging system, it is important to comprehend all the possible attacks and breaches which an IT platform could face, so that contingencies can be formulated accordingly. It would not only the developers in drafting the most appropriate response but also enable the platform to proactively mitigate any prevalent cyber risks.
A brief description of the multiple types of cyber-attacks and relevant system breaches is given as follows:
-
Compromised Credentials - Being the most commonly used type of access credentials, compromised usernames and passwords can allow unauthorized entities to access valuable information, policies, and architectures that can be modified as per the requirement, with the ultimate aim of causing maximum damage.
-
Weak & Stolen Credentials – Use of weak passwords or their reuse can result in the exposure of the same to hackers, who can utilize these for lateral movement. It becomes crucial in IoT settings where the whole eco-systems could get disturbed by any such malicious activity.
-
Malicious Insiders – Generally from the pool of unhappy employees of any organization, malicious insiders can expose or leak private and confidential enterprise information to competitors or third parties.
-
Missing or Poor Encryption – Consisting of the conversion of plaintext into ciphertext, missing or poor encryption could result in sensitive information being communicated over insecure internet channels and can ultimately result in an interception and the subsequent negative consequences.
-
Misconfiguration – Labeled as an error in system configuration, if the system’s usernames and passwords are used, hackers can easily identify and exploit the relevant flaws and gain access to the information which can certainly be leveraged.
-
Ransomware – Categorized as cyber extortion, ransomware is a technique via which users can’t access their valuable data unless a hefty ransom is paid. Cybercriminals usually take this amount in the bitcoins to avoid traceability.
-
Phishing – Being the most commonly used cybercrime tactic, phishing entails contacting the target user via email or messages while impersonating a legitimate service provider to extract valuable information like usernames, passwords, and credit/debit card details.
-
Trust Relationships – Characterized by the seamless trust existing amongst the system and the users, trust relationships can allow the users to log in multiple domains using a single domain authentication; trust exists between multiple internet domains that’s why reauthentication isn’t done. These relationships can certainly breach the security parameters, required for a secure messaging platform.
Why Dastafilez?
Data rooms can be considered an extension of secure communication systems; a data room is essentially a space in a secured environment used to store and confidential data in a secure fashion. These rooms can be physical as well as virtual, while latter being characterized by lower setup and operational costs, global accessibility, and preservation of documents.
Dastafilez, an innovative virtual data room, offers one of its kind solutions to offer privacy and protection of classified information via multi-factor authentication, end-to-end encryption, and advanced authorization modules. It essentially is a platform with controlled access management to share any important information or documents in a secure manner.
Features of Dastafilez
Being a cloud-based data room platform, Dastafilez offers a host of innovative features which certainly form the unique selling propositions for the subject application. Unlike other communication applications, Dastafilez operates on true end-to-end encryption i.e., encryption is not an opt-in feature, rather is implemented across the board for all the relevant information records and subsequent sharing. Coupled with the features of Zero-Knowledge Architecture and Immutable audit trails, Dastafilez stands out to be a strong contender in the domain of secure communication platforms.
Zero-Knowledge Architecture
Laying its foundations on data rights management, Dastafilez utilizes the zero-knowledge architecture; an innovative multi-level asymmetrical cryptography to make sure that only the authorized members have access to the documents. All the documents and classified data are encrypted before sharing over an insecure channel. With the framework, not even the system architects and network administrators have the visibility of passwords or the stored information, owing to their encrypted nature. Being a cloud-based platform, Dastafilez offers a contingency security plan as well; if the protocols are breached, hackers won’t be able to read the encrypted information or decrypt the master password. It certainly acts like an unbreachable storage vault.
Immutable Audit Trail
As cyber threats are evolving every day in terms of complexity and scope, most cybersecurity and risk management frameworks entail the “audit trail” of every user activity. These audit trails are generally stored in relational databases, which owing to their technical architecture can easily be modified, and can result in a lack of trust amongst the operating entities. Due to this risk, enterprises opt for manual storage of records, which might generally get reviewed by 3rd party auditors and result in inefficient, costly, and non-optimal processes. Dastafilez gives its clients the flexibility to store the audit trail on a blockchain which is complemented by an immutable audit trail; “timestamp” really provides the visibility of what actually happened, when, and how. The immutable ledger of transaction records can be fetched as per the requirements of the enterprises.
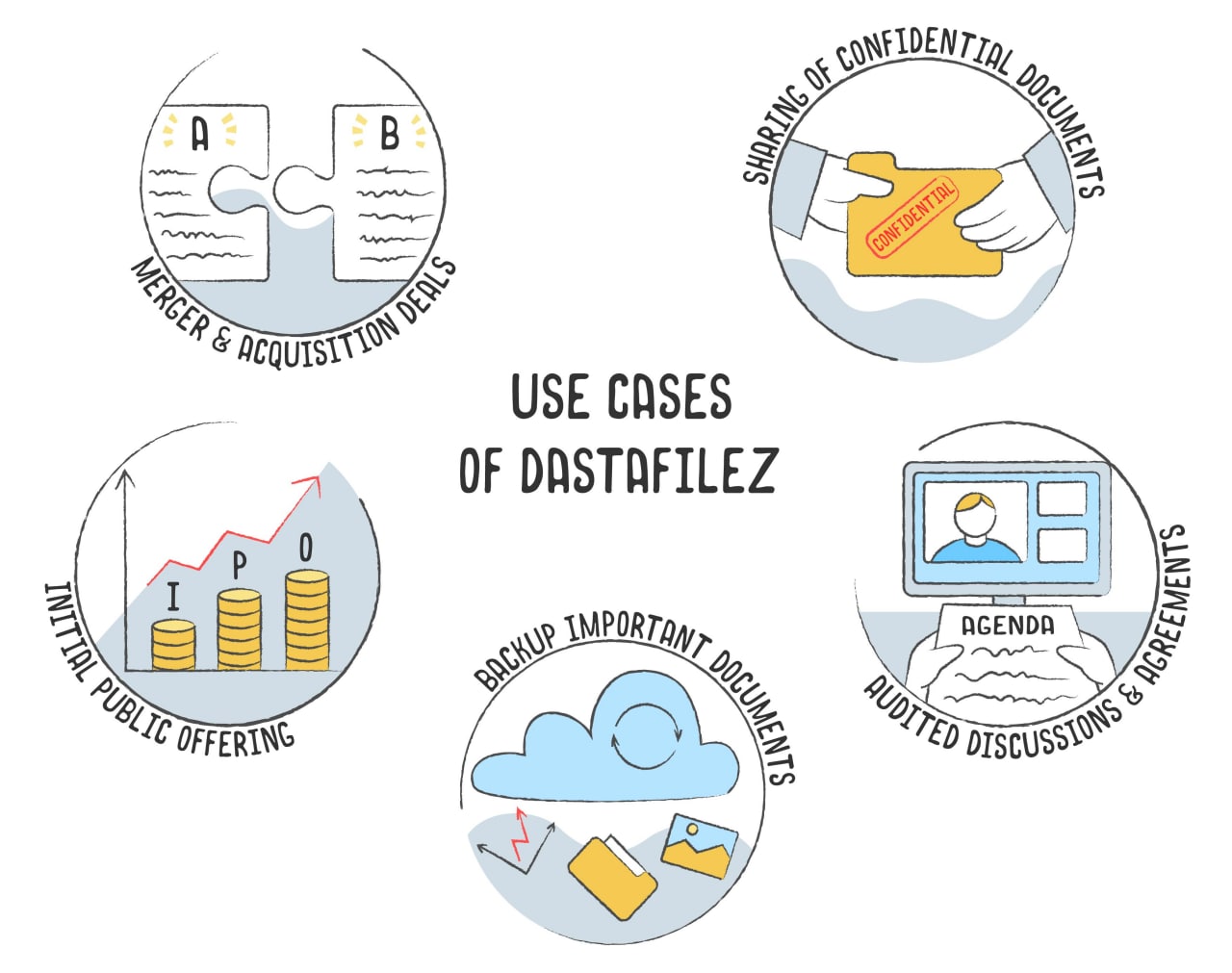
Use Cases of Dastafilez
Dastafilez, a virtual data room, providing data confidentiality, privacy and integrity can be used in a host of applications. The multi-faceted application of Dastafilez is particularly useful in the following use-cases:
1. Merger & Acquisition Deals
With the ever-evolving business dynamics, mergers and acquisitions are common to achieve the synergies for business success. For mergers and acquisitions to happen, an in-depth analysis of all the classified information is required from both entities. The requisite need can be fulfilled most efficiently by Dastafilez, building upon its zero-knowledge environment; the authorized users can access the documents for viewing and sharing purposes without the risk of any security breaches so that data confidentiality and integrity can be ensured. Dastafilez provides ease of access and simple-to-use frameworks to fulfill all the merger and acquisition documentation requirements in the most secure manner possible.
2. Sharing of Confidential Documents
Owing to the existence of backdoors in hardware as well as the software component of the IT infrastructures, sharing classified documentation over the internet channel is always a risky task. Dastafilez provides users the flexibility to share all such documents with confidence as end-to-end encryption and immutable audit trail based upon the blockchain framework make any malicious threats null and void. Dastafilez also serves as a secure, unbreachable vault where the strategic reports and documentation can be stored and can easily be retrieved as well in a hassle-free manner.
3. Initial Public Offering
When an enterprise decides to go public, a lot many stakeholders require access to all the relevant documentation for the accurate and precise valuation of the company. This information can be confidential or classified while stakeholders might entail attorneys, investment bankers, regulatory bodies representatives, etc. Dastafilez can make sure that all these entities get the required information with ease of access while ensuring no data breach takes; not only integrity of the documents is guaranteed but also the flexibility of access control makes the process streamlined and productive.
4. Audited Discussions & Agreements
Dastafilez provides the additional functionality of recording negotiations, discussions, and debates on the blockchain i.e., in an immutable manner. These records can easily be decrypted as and when required by the users, based upon the relevant authentication and authorization. It all can be done without trust in Dastafilez.
5. Backup Important Documents
Though solutions like Google Drive and DropBox are available for storage purposes, data stored in these platforms is still susceptible to attacks owing to the unencrypted cloud services. Dastafilez stores all the records, information, and documents in the end-to-end encrypted form, free of any associated cyber risks. Due to these properties, it can also be used to record the creation of intellectual property like music, art, compositions, etc., via timestamps based upon the blockchain.
Final Thoughts
As information technology is touching every facet of human life, it is important to make sure that information sharing serves its intended purpose and isn’t misused by malicious parties for any of their malicious motives. Virtual data rooms provide efficiency in data storage and sharing while ensuring maximum security checks are in place. Dastafilez is a cloud-based data room that offers end-to-end encrypted communication services; it features the advanced security frameworks of zero-knowledge architecture and immutable data trail to guarantee confidentiality, integrity, privacy, and non-repudiation of the data records and information. Many big enterprises are also offering similar services but with very high pricing and that too with end-to-end encryption as opt-in mode. Thus, Dastafilez is an offering that can transform the business process of any-sized business enterprise while offering top-of-the-line security features. Given the scope of services being offered, Dastafilez can easily guarantee a very high ROI for the relevant organizations.
